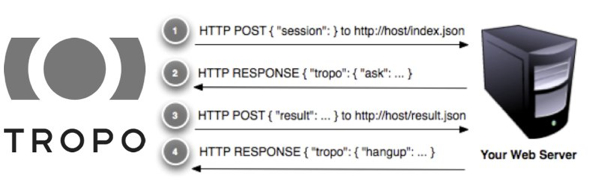
#1 – request
Request is the easiest way to make REST calls. It runs server-side to hide your token and if you use Postman to test the HTTP request, it can even generate the code for you!
https://www.npmjs.com/package/request
Example Request Using Spark Messages API:
var request = require(‘request’);
var req = {
auth: { bearer: ‘sparkTokenHere’ },
url: ‘https://api.ciscospark.com/v1/messages’,
json: true,
body: {
‘roomId’: roomId,
‘text’: message
}
};//end setuprequest.post(req, function(err, res) {
if(err) {
console.log(err);
} else {
}
});//end rest call
#2 – picker
Picker is a server side router for Meteor that works alongside middleware to easily provide an API or webhook into your application.
https://atmospherejs.com/meteorhacks/picker
Example Webhook with JSON parsing using body-parser:
Picker.middleware(bodyParser.json());
Picker.middleware(bodyParser.urlencoded({extended: false}));
Picker.route(‘/myWebhook’, function(params, request, response) {
personEmail = (request.body.data.personEmail);
msgid = (request.body.data.id);
#3 – Q
Before getting too far ahead with node.js, you’ll need to grasp the underlying language, javascript. Javascript is a synchronous language, meaning it runs functions all at the same time, which can make a mess of things if you don’t use callbacks properly. Q uses something called promises to run things asynchronously in the order you tell it. To learn more about callbacks and why this package is so necessary, check out callbackhell.com
http://documentup.com/kriskowal/q/
Example of promises with Q:
Q.fcall(promisedStep1)
.then(promisedStep2)
.then(promisedStep3)
.then(promisedStep4)
.then(function (value4) {
// Do something with value4
})
.catch(function (error) {
// Handle any error from all above steps
})
.done();
#4 – bert
Bert makes notifications simple
https://github.com/themeteorchef/bert
Bert.alert({
title: ‘Conference Now’,
message: ‘Connecting to Tropo…’,
type: ‘info’,
style: ‘growl-bottom-right’,
icon: ‘fa-phone’
});
#5 – fontawesome
fontawesome is a collection of 675 icons in unicode that can be embedded in your site with a single tag. Most people will use their built in CDN (content delivery network) to make deployment even easier.
http://fontawesome.io/icons/
<i class=fa fa-camera-retro”></i>
#6 – nodemailer
nodemailer is the best email package hands down. It supports an html body and allows you to specify options within the app.
https://www.npmjs.com/package/nodemailer
var nodemailer = require(‘nodemailer’);
// create reusable transporter object using the default SMTP transport
var transporter = nodemailer.createTransport(‘smtps://user%40gmail.com:pass@smtp.gmail.com:587’);// setup e-mail data with unicode symbols
var mailOptions = {
from: ‘”Fred Foo 👥” <foo@blurdybloop.com>’, // sender address
to: ‘bar@blurdybloop.com, baz@blurdybloop.com’, // list of receivers
subject: ‘Hello ✔’, // Subject line
text: ‘Hello world 🐴’, // plaintext body
html: ‘Hello world 🐴‘ // html body
};// send mail with defined transport object
transporter.sendMail(mailOptions, function(error, info){
if(error){
return console.log(error);
}
console.log(‘Message sent: ‘ + info.response);
});
#7 – validator
Need to check if an email is actually an email? A dollar amount is actually a dollar amount? Validator has a ton of built-in methods to check for you.
https://www.npmjs.com/package/validator
var validator = require(‘validator’);
validator.isEmail(‘foo@bar.com’); //=> true
#8 – csv
While ECMA 5 has native XML and JSON support, a lot of Cisco applications still rely on CSV (comma seperated values). This package aims to bridge the gap.
https://www.npmjs.com/package/csv
var csv = require(‘csv’);
csv.parse(data, function(err, data){
csv.stringify(data, function(err, data){
process.stdout.write(data);
});
});
#9 – bootstrap
Boostrap is so useful, I wish it was just included in HTML period. Any buttons, menus, fonts, tables, grids, layouts, etc. are super easy with Bootstrap.
https://www.npmjs.com/package/bootstrap
Just include the bootstrap code below to utilize their CDN:
<!– Latest compiled and minified CSS –>
<link rel=”stylesheet” href=”https://maxcdn.bootstrapcdn.com/bootstrap/3.3.7/css/bootstrap.min.css” integrity=”sha384-BVYiiSIFeK1dGmJRAkycuHAHRg32OmUcww7on3RYdg4Va+PmSTsz/K68vbdEjh4u” crossorigin=”anonymous”><!– Latest compiled and minified JavaScript –>
<script src=”https://maxcdn.bootstrapcdn.com/bootstrap/3.3.7/js/bootstrap.min.js” integrity=”sha384-Tc5IQib027qvyjSMfHjOMaLkfuWVxZxUPnCJA7l2mCWNIpG9mGCD8wGNIcPD7Txa” crossorigin=”anonymous”></script>
#10 – jsPDF
PDFs are still the industry standard for “digital hard copies” of documents. jsPDF makes generating PDFs easy.
https://parall.ax/products/jspdf
<script src=”https://cdnjs.cloudflare.com/ajax/libs/jspdf/1.3.2/jspdf.debug.js”></script>
var pdf = new jsPDF();
pdf.text(30, 30, ‘Hello world!’);
pdf.save(‘hello_world.pdf’);